Survived WannaCry? Now What?
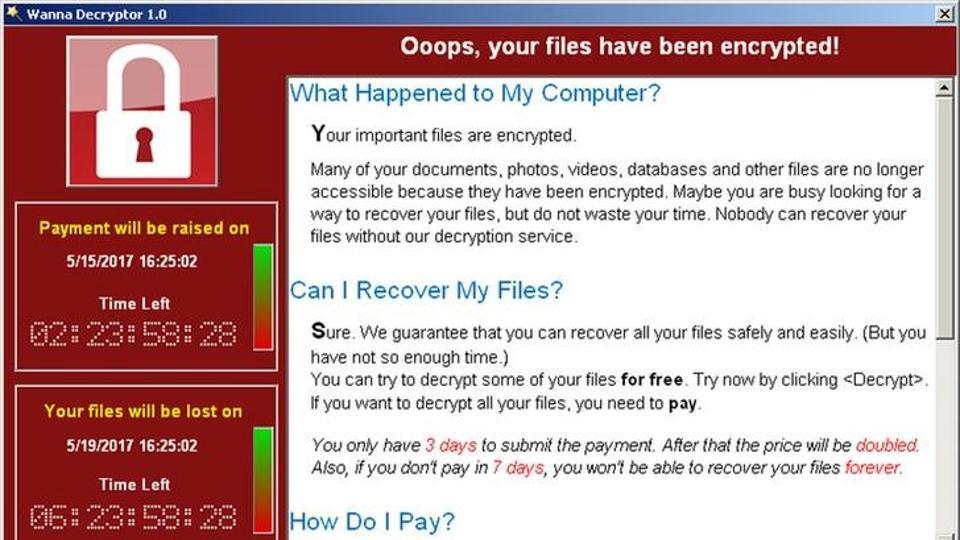
So, you survived WannaCry ransomware attack, now what do you do to avoid the next attack?
WannaCry targeted a vulnerability that existed in Windows from XP to the latest version of Windows 10 using an exploit developed by the NSA. Microsoft released a patch back in March, but many organizations failed to update.
The widespread impact of this attack should be a wake-up call to businesses, governments and consumers alike. It needs to be a reminder that operating systems be updated when vendors release security updates, in addition all data backed-up to multiple locations and on a regular basis.
However, another important component on protecting your systems is the proper use of firewalls. Every Windows systems has a built-in firewall and with the correct configuration provides one layer of protection. In the case of WannaCry, blocking TCP port 445 would have helped mitigate the attack.
But the best defense is blocking any such attack before it gets into your network. Next Generation Firewall technologies, with the various protections, help mitigate such an attack based on a known vulnerability, but also a zero-day attack. Implementing Intrusion Prevention signatures against known exploits and utilizing NGFW vendor signature updates as soon as they are released reduces your attack surface. Configuring and utilizing best practices such as DNS Sinkholing, along with the other capabilities of your NGFW, such as URL filtering helps protect your network.
Everyone needs to do a post-mortem of this incident, whether affected or not, with a focus on the protections and security measures currently in place. Are they adequate to protect you against the next attack or do you need to make changes?
WannaCry, while impacting thousands of users and systems, was not as bad as it could have been, however the next attack, if based on a new or zero-day exploit could have a much greater impact and do significantly much more damage.

Comments are closed